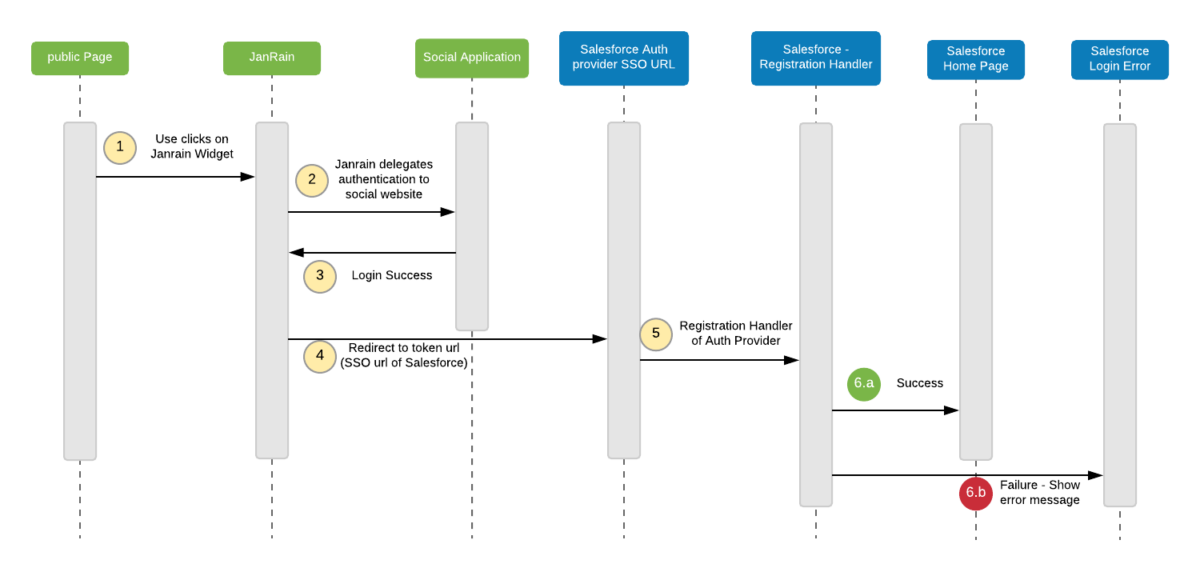
Tag: Single Sign On
-
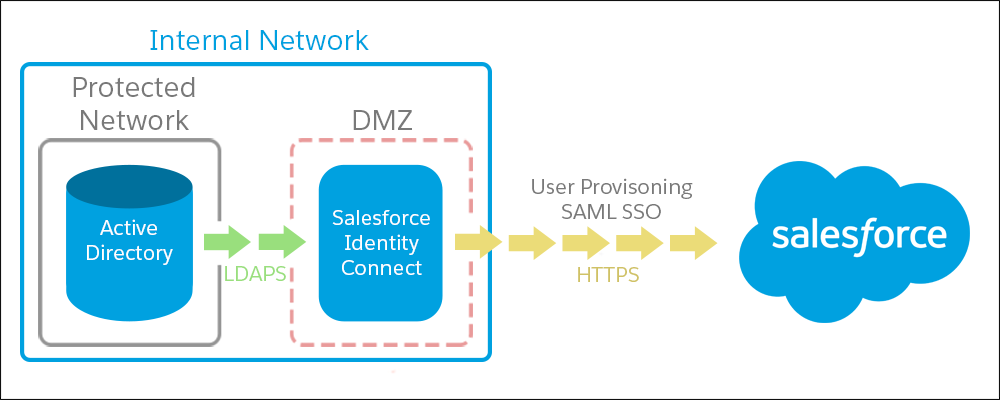
Quick Summary of Salesforce Identity Connect Capabilities
Short & quick note about Salesforce Identity product
-

Video – Use Microsoft Azure’s Active Directory as Identity Provider for Salesforce SSO in 15 Minutes
Video tutorial on how to use Microsoft Azure’s Active Directory as a Identity Provider for Salesforce. It uses Federated Single Sign On (SSO) feature of Salesforce
-
Step by step guide to Setup Federated Authentication (SAML) based SSO in Salesforce – Video Tutorial
In this post, We will be dicussing how to setup Federated SAML based Authentication in Salesforce. SAML stands for “Security Assertion Markup Language” and it is Open standard for exchanging Authentication and Authorization between Systems. SAML based authentication is supported by all editions of Salesforce. User Validation can be initiated by any one of below two…