Below are important summary about Identity Connect
- It comes as add on feature with Salesforce with additional cost
- Only works with Active Directory
- Its only one way Sync, from Active Directory to Salesforce
- We can assign profile, role and permission set to user using Identity Connect
- Any changes made manually for mapped field on user record would be overwritten with next sync.
- Sync from Active directory to Salesforce can be realtime or scheduled
- If the user is deactivated in Active Directory then user record also gets deactivated. Identity Connect internally uses API to deactivate user. Unlike for some other SSO solutions, if user is deactivated in Active directory then they cannot login to Salesforce. However, if they already logged into mobile phone or connected app then they can still access Salesforce. This problem is resolved in Identity Connect.
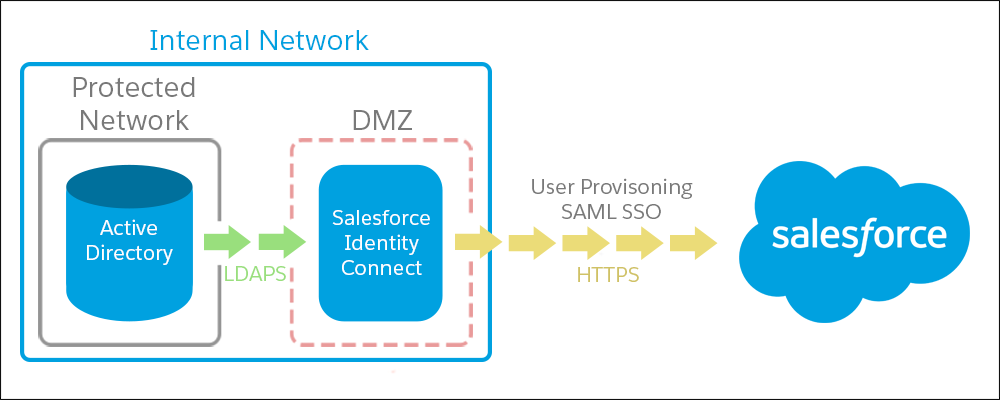
- Identity connect is installed on client network behind the firewall. Identity connect pushes the changes to Salesforce from client’s network.
- If we want to use Identity Connect as a SSO and user wants to use Salesforce from outside company network or on mobile phone, then its login page must be accessible on internet. This can be done by installing Identity Connect on De-militarized Zone (DMZ).
- Identity connect is used for User provisioning but not for Just in Time (JIT) provisioning.
- We can use Identity connect as a SSO. If customer already has SSO implemented then Identity connect can only be used for user provisioning.
- One Identity Connect can be used for multiple Salesforce instances however all production or all sandboxes. If you want to use Identity connect for production and Sandbox at same time, then we would need two Identity Connect, one for Sandbox and other for Production.
- Identity Connect will work with only one Active Directory but it can have multiple domains in same AD.
- Integrated Windows Authentication (IWA) is supported by Identity Connect using Kerberos authentication protocol. Means, if user is already logged into company provided windows system, then login screen would be bypassed and Salesforce login experience would be seem less.
- Scheduled sync uses more API’s then realtime schedule. Because, Schedule sync checks for changes in all Salesforce users vs all AD users.
Resources
Leave a Reply to Prabhakar MohanCancel reply